Appearance
LAPS (Local Administrator Password Solution)
In many Active Directory environments, the same local administrator password is used across all computers in the domain. This creates a significant security risk, as an attacker gaining access to one system can potentially use the same credentials to move laterally to other systems. To address this, Microsoft introduced the Local Administrator Password Solution (LAPS), designed to securely manage local administrator passwords on domain-joined computers.
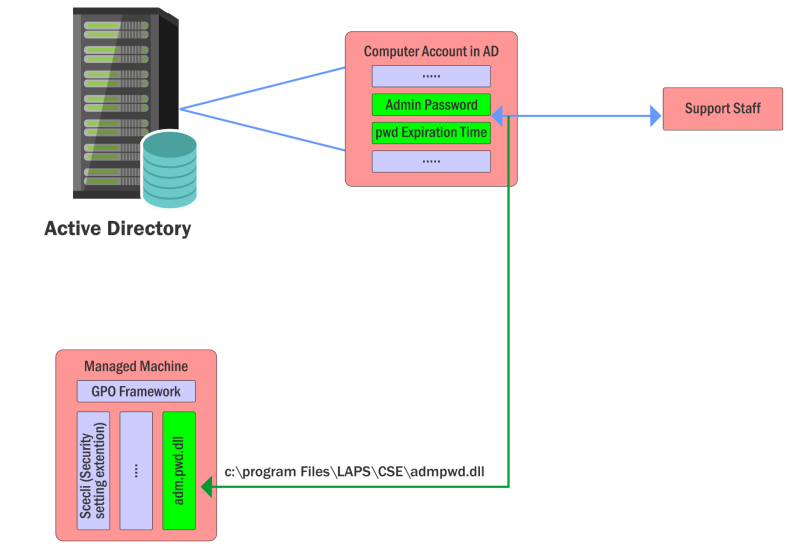
LAPS automatically generates a unique password for the local administrator account on each computer and stores it in Active Directory. This solution should help to prevent lateral movement and privilege escalation by ensuring that all local administrator passwords are unique.
 Local Administrator Password Solution (LAPS)
Local Administrator Password Solution (LAPS)
The password is stored in the ms-Mcs-AdmPwd attribute of the computer object. By default, only members of the Domain Admins group can read this attribute. This could be problematic, if not configured properly. This is because as an normal user you can enumerate on what computers the LAPS is enabled and which users can read the password. Once you enumerate that, you have a list of attractive targets to move laterally.
Enumeration
On a domain-joined computer with LAPS enabled, the file C:\Program Files\LAPS\CSE\AdmPwd.dll will be present. This DLL is responsible for managing the local administrator password.
To find users who can read the passwords in clear text machines in OUs:
powershell
Get-DomainOU | Get-DomainObjectAcl -ResolveGUIDs | Where-Object {($_.ObjectAceType -like 'ms-Mcs-AdmPwd') -and ($_.ActiveDirectoryRights -match 'ReadProperty')} | ForEach-Object {$_ | Add-Member NoteProperty 'IdentityName' $(Convert-SidToName $_.SecurityIdentifier);$_}powershell
Get-LAPSPasswords.ps1powershell
Import-Module C:\Tools\AdmPwd.PS\AdmPwd.PS.psd1
Find-AdmPwdExtendedRights -Identity OUDistinguishedNameAbuse
Once you compromise an account which has the rights to read the LAPS password, you can use the following methods to read the cleartext password:
powershell
Get-DomainObject -Identity <targetmachine> | select -ExpandProperty ms-mcs-admpwdpowershell
Get-ADComputer -Identity <targetmachine> -Properties msmcs-admpwd | select -ExpandProperty ms-mcs-admpwdpowershell
Get-AdmPwdPassword -ComputerName <targetmachine>